|
|
About ISO/IEC 29128
|
|
ISO/IEC 29128 (Verification of Cryptographic Protocol) is a standard that prescribes inputs and outputs to and from tools for safety assessments of cryptographic protocols and specifies the protocol assurance level in accordance with the descriptions’ accuracy.
|
Inputs and Outputs in Protocol Assessments
|
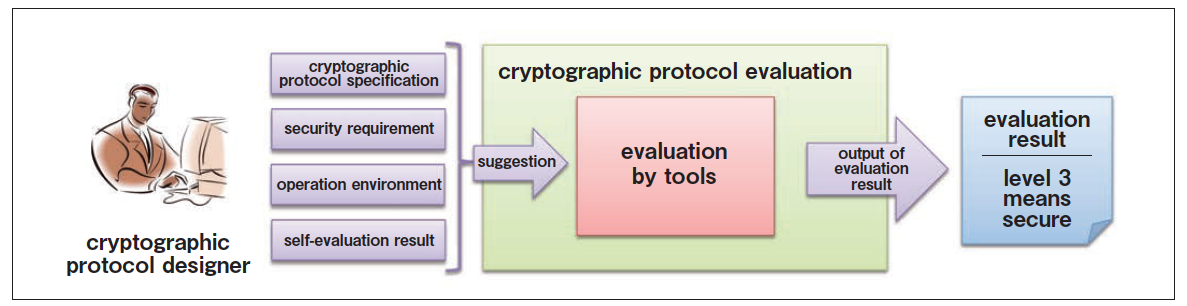
The following three information items are to be input for an assessment of a cryptographic protocol based on ISO/IEC 29128.
- Protocol Specification: Specification of the protocol
- Operational Environment: Environment for executing the protocol (actions attackers can take)
- Security Property: Security requirements that need to be fulfilled
The Protocol Specification is a formal description of the cryptographic protocol to be assessed. Information about processing in the entity on which the protocol is executed, such as encryption, decryption, attachment of an electronic signature, verification, and whom individual data are sent to in what order is to be described in a language specified for the tool.
The Operational Environment is an environment for executing the protocol and mainly describes actions that attackers can take against the protocol. Examples of such actions include eavesdropping and falsification of communicated data, and creating and sending arbitrary data to participants in the protocol.
The Security Property is a description of security requirements to be fulfilled by cryptographic protocols to be assessed. Inputs to the tool may include descriptions of circumstances that must not occur. Examples of these include leakage of information that must be kept confidential and successful impersonation.
When these pieces of information are input to a cryptographic protocol assessment tool, the tool processes it and outputs the assessment results. When the possibility of “circumstances that must not occur” described in the Security Property is not found, the tool will give output to that effect. When such possibility is discovered, the tool will output the process in which such circumstances will occur. This process may be regarded as the attacking procedure.
|
Protocol Assurance Level
|
Concerning the input and output to and from the tools mentioned above, ISO/IEC 29128 prescribes four Protocol Assurance Levels (PALs) based on the accuracy of their expressions. When the descriptions are more accurate the protocol is handled as PAL4. When the descriptions are vague the protocol is treated as PAL1. If the possibility of attack is not discovered in the outputs from these tools the tools are regarded as safe in the respective PALs.
What must be noted here is that these assessments do not mean that a safe PAL4 protocol is safer than a safe PAL1 protocol, but rather that the possibility of attack was not found in the former in a more accurate assessment. Therefore it is not necessarily possible to compare the safety of PAL4 with that of PAL1. Generally, a high-PAL protocol is used to assess systems that handle important information.
Protocol Assurance Level Levels Assessed by Using the Formalization Method(ISO/IEC 29128)(PDF)
|
|



